Facebook Two Factor Authentication bypassed when logging in multiple times
Facebook has the option to provide additional security by using 2FA during the login process. In fact, Facebook offers better options than most; even offering U2F support. Unfortunately, there are still issues that allow bypassing 2FA in some cases.
Facebook prompts for security key authentication during login.
Bypassing 2FA as a Feature
Many sites offer to allow logging in without the additional 2FA step after authenticating with 2FA.
Facebook also offers this feature. In fact, it's the default option. After authenticating with 2FA, Facebook asks if it should require 2FA when logging in again from the same browser. If you select the Don't Save option, you would expect 2FA to be required during the next login.
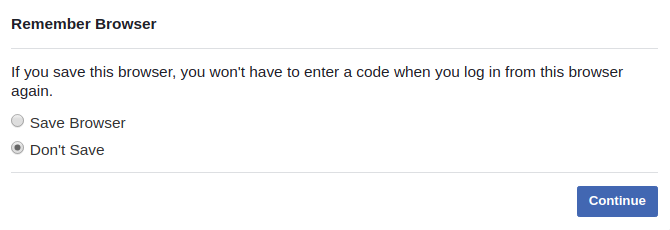
Selecting Don't Save option when asked to remember browser.
Facebook Defies User Security Expectations
In actuality, this option appears to be ignored. Try logging out and then logging back in. You'll simply log back into facebook. No 2FA required. The same problem happens with text message 2FA, and I assume other 2FA methods as well.
It does appear to eventually forget your browser. If you wait awhile you may get asked to provide 2FA on your next login. This still defies expectations and there is no indication as to how long you must wait before your browser is forgotten.
The only way to ensure that your 2FA isn't remembered is to delete Facebook related browser data. Using 'Private' browsing or similar browser feature that will delete local data after closing the browser is another workaround.
This is Actually a Security Problem
I reported this issue to Facebook in November of 2017, and the reply was that this was only a 'theoretical' attack, and that you should not allow others to access your device. The bug still hasn't been fixed.
While it's a valid point that if a user's device is compromised you cannot prevent many attacks, this bug bypasses one of the major features of 2FA: Preventing trivial keylogging or replay attacks when a single device is compromised. This is especially problematic for public or shared computers. Not everybody has access to a personal computer, but with an authentication token you can minimize risks to a greater extent than merely using a password.
It's possible to create specialized software to compromise an account even with 2FA, or even modify a user's session, but that isn't even necessary in this case. A simple keylogger and accessing leftover browser data is all that's required to impersonate a user.
This Should Be Easy to Fix
This should be any easy fix: Just make the Remember Browser feature actually work! Telling a user that something works one way, and then doing something else deceives the user in a way that impacts their account security.